When it comes to protecting your information online, passwords are the most-used form of authentication for websites and applications alike. However, passwords are also one of the most insecure forms of user authentication out there.
Upon registration, users create a unique ID and key (typically a username and password) that are then stored securely on the website’s server. Ideally, the user is the only person with knowledge of their password, making it so that they’re the only one able to access the account. When the user re-enters their credentials, they are checked against those stored in the web server and, if they are a match, the user is verified.
The challenge is that since passwords are so widely used, the number of insecure accounts is substantial. Not to mention, passwords can provide a false sense of security when users are woefully unaware of the vulnerabilities they bring. Passwords are not only difficult to manage on a personal level but can also cause large-scale data breaches when they are easily guessed or cracked by hackers.
Furthermore, if your business is using passwords to protect internal accounts and your user database, you and your user’s sensitive data could be at risk.
There’s a lot to unpack here! Before we jump in, let’s walk through some of the most commonly asked questions and answers when it comes to password-based authentication.
Password Authentication FAQs
What are the three types of authentication?
Authentication is the process that ensures the individual requesting access to a system, website, or application is the intended user. There are three main methods used for authentication purposes:
- Knowledge-based: Also referred to as “something you know.” This category includes traditional passwords. When a user creates a unique password for their account, it then becomes the key to re-enter that account time and time again. It’s something that the user (and hopefully only the user) knows.
- Possession-based: Also referred to as “something you have.” In this scenario, an individual verifies their identity using something that only the intended user would have. For example, a user could swipe a physical key card or prove access to a separate personal email account to show that they are who they say they are.
- Inheritance-based: Also referred to as “something you are.” These are typically biometric characteristics such as a fingerprint or facial scan that is then used to verify the user’s identity.
Without these authentication processes, sensitive user information would be available on the web with no restrictions, meaning it could easily fall into the wrong hands.
What is password authentication?
Password authentication is a process that involves a user inputting a unique ID and key that are then checked against stored credentials.
You’ve likely been asked to create and/or enter a password to gain access to a personal account, whether that’s a social media platform or an online banking tool. When you do so, you’re taking part in a password authentication system that keeps your sensitive information safe from unauthorized users.
The idea is that only the person who created and set the password will know it and be able to repeat it, thus verifying their identity as the original user and providing access to restricted data and resources.
Say Goodbye to Passwords
and
Hello to Secure Logins.
Go passwordless and delight your users with secure and seamless one-click login.
How are passwords stored?
When a user creates a password, a copy of that credential is stored by the system or website in a secure password database against which the server can compare any further login attempts. Because all those passwords are stored in a centralized location, (which would be a field day for hackers) it’s important that password-based authentication systems ensure top-notch security for those databases.
Typically, passwords are stored in an encrypted fashion so that even if a hacker is able to access the database, the information they see would be of no use to them. This is called salting and hashing your passwords, which we’ll get into further detail below.
What are password alternatives?
A password alternative is any sort of authentication protocol that doesn’t utilize a typical ID and key to grant users access. Going back to the three types of authentication, password alternatives often fall into possession or inheritance-based methods.
Our favorite password alternative (in fact, our favorite authentication method overall) is email authentication. For websites and applications that offer Swoop’s email authentication as a password-free alternative, users can simply verify their identity by following a pre-determined action (such as using Swoop’s Magic Link™ or Magic Message™) from their personal email account.
Whether your organization is set on using password authentication or you’re exploring passwordless alternatives, it’s important to be aware of a password’s weaknesses so that you can find a secure way to protect your data.
That’s why we’ve compiled a list of top password authentication vulnerabilities as well as these recommended ways your company can avoid them:
We’ll explain each weakness in more depth and provide top tips for improving your website’s security. Ready to jump in? Let’s get started!
1. User-Generated Credentials
How do user-generated credentials pose a threat?
Since users have to create their own passwords, there’s always a chance they won’t create secure credentials. In fact, around 90% of user-generated passwords are considered weak and easily vulnerable to hacking.
Whether it’s because users want to have a password that’s easy to remember, they aren’t up to date on password security best practices, or subconsciously (and even consciously) use patterns to generate their passwords, this type of authentication has its flaws.
Even if your website is equipped with a password strength-checking tool, (like the ones below) the results can be inconsistent and inaccurate, often leading users into a false sense of security.
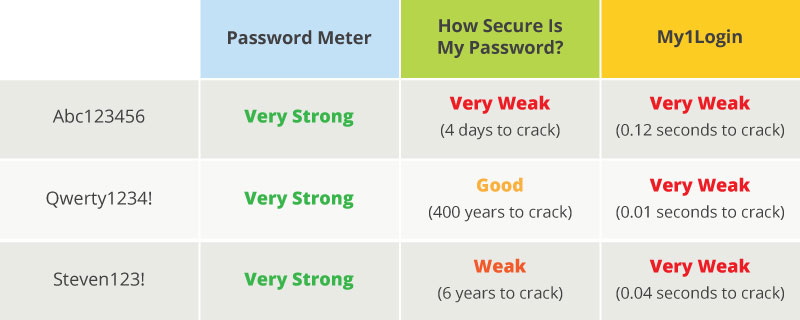
Creating complex passwords is difficult because our minds are drawn towards patterns. Think about the passwords you create. They likely all follow a similar formula, like using a word with numbers and a special character at the end.
While these patterns make it easier for us to remember our credentials, cybercriminals are also aware of the common formulas people use to create passwords. As a result, hackers can use this knowledge to adjust how their brute-force systems run through password combinations or crack your password making an educated guess.
How can I secure user-generated credentials?
Password authentication isn’t secure enough on its own because it puts the (likely, uninformed) user in charge of protecting their sensitive information. Instead, web developers need to take the initiative to ensure their users’ data is protected in other ways.
If your website continues to use passwords in your website authentication system, you should consider offering some alternatives or multi-factor systems to add some additional levels of security.
For example, email authentication is an easy and effective way to offer your users a safer way to engage with your site. Email clients already employ tighter security protocols than most other websites can offer in addition to built-in two-factor authentication, so the credentials tend to be relatively secure. Some users might shy away from these options, but offering them in addition to other authentication systems will boost security all-around.
Additionally, developers should make a point to scan all newly created passwords through a list of commonly used or compromised credentials. When a user tries to create new credentials using a weak password, they’ll be asked to use a different credential before proceeding.
Take a look at this chart with some best practices for ensuring password security. When your team implements criteria such as these into the back-end of password requirements, it can reduce the number of insecure credentials that get through.

As a result, users are forced to create stronger passwords and avoid those that can be easily guessed. However, it’s important that your team stays up-to-date with all the latest password protection protocols, as best practices are constantly evolving alongside authentication technology.
Where can I learn more?
Are you looking for a more in-depth look at password authentication and the ways you can tighten your website’s security? Check out our comprehensive guide to the modern password.
2. Brute-Force Attacks
How do brute-force attacks pose a threat?
Simply put, a brute-force attack occurs when a computer program runs through every password combination until they find a match. The system will run through all one-digit combinations, two-digit combinations, and so forth until it cracks your password. Some programs specifically focus on combing through the most commonly used dictionary words, while others target popular passwords against a list of possible usernames.
As technology evolves, so do the tools hackers use to crack people’s credentials. Aside from merely guessing your password, a brute-force attack is the most common technique hackers use.
To make matters worse, these systems are able to run through thousands of combinations in less than a second, which means that shorter passwords can be cracked in a very short time frame.
How can I secure against brute-force attacks?
The first thing you should do is ensure that hackers can’t use brute-force attacks for individual accounts. Companies can achieve this by limiting the number of login attempts and password reset requests for every account and IP address range.
Your security team will need to establish a few standards before you can implement this process. For instance, you’ll need to ask yourself:
- How many login attempts and password reset requests will each user and IP address receive? The limit for IP addresses should be more than the limit for users. This is because multiple accounts could be using the same IP address, such as in an office setting.
- How long will the account be temporarily blocked? Once a user has reached the allowed number of requests, the account should be blocked for a short period of time. The recommendation is 10-15 minutes, although you may choose to go higher or lower than that.
- When should we block an IP address from making login attempts? If there has been a lot of unusual behavior from a specific IP address, it might be in your website’s best interest to permanently block it from making login attempts. However, blocking IP addresses also runs the risk of excluding real users, so you’ll want to be careful.
In addition to making these changes, it’s also important that you encourage users to create longer and stronger passwords, as recommended in the previous section. This is because the longer a user’s password is, the longer it will take for a computer to gain access. And hopefully, your system will be able to lock the hacker out before that even happens!
Where can I learn more?
Securing your login process is the first step to improving your password authentication. Luckily, there are pre-built tools ready to help you do so. Check out our list of top WordPress login plugins to help you secure your website.

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
3. Recycled Passwords
How do recycled passwords pose a threat?
Recent online security best practices suggest that users create passwords that are at least 8 characters (the ideal number is around 12 characters long) and use a combination of uppercase and lowercase letters, numbers, and symbols.
What’s more, every password should follow these best practices and be unique to each account. Meaning no repeats!
This might be doable if users only had to manage one or two personal accounts. But the reality is that the average internet user juggles over 90 online accounts, and that trend is only projected to increase in the coming years.
The challenge with passwords is that in order for them to be secure, they need to be complex and unique. However, complex passwords are hard to remember, which means that passwords can’t be effective or user-friendly, let alone for nearly one hundred accounts. It really is a lose-lose situation.
Moreover, people can’t remember that many passwords, so they have to use other strategies to store their credentials, such as low-tech solutions like a sticky note, spreadsheet, or document, or high-tech password managers.
The low-tech solutions are just that, which leaves these materials easy to steal. High tech password managers allow users to securely store all their passwords in a centralized location, but there is a monetary cost, steep learning curve, and device-based compatibility issues which make this solution less than viable for most users.
Don’t forget, this solution has its own risks, as most of these tools require users to create an account with password-protection. If a cybercriminal gets the password for your management tool, he’d have access to all of your accounts.
How can I secure against recycled passwords?
Because it’s wholly unrealistic to expect users to manage 90-something unique passwords, one effective solution is to encourage users to connect multiple accounts with a single, ultra-secure password.
For example, we already mentioned that email clients tend to have stronger password security regulations. It makes sense to use that as a tool to authenticate further online accounts as well. However, social media platforms such as Facebook and Twitter have also become popular resources for streamlining the registration and login processes.
Swoop’s passwordless technology uses email authentication to securely verify users in one of two easy ways:
- Magic Link™: The Swoop team automatically sends a Magic Link™ to the user’s personal email account. When the user clicks that link, their identity is verified and they’re granted access to the account without a password.
- Magic Message™: The user clicks a mailto link which opens and sends a pre-written message from their own email, which verifies their identity and provides access to the new account without a password.
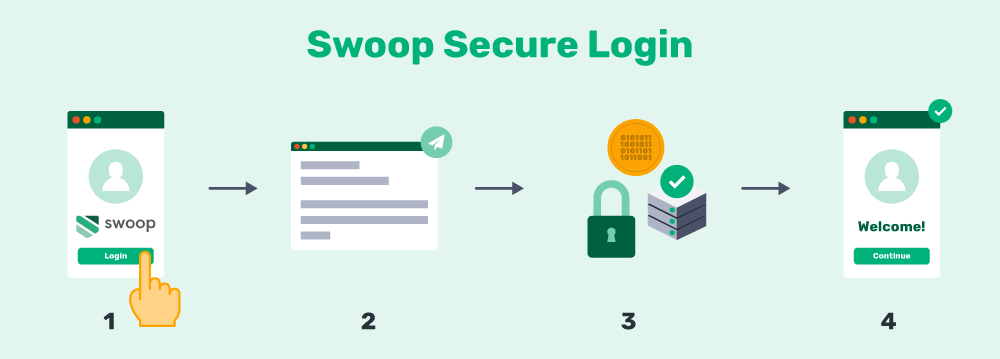
Behind the scenes, Swoop’s technology conducts three layers of security measures to determine if the email came from the correct user. By implementing an authentication method like this, users will only have to manage the password for their email address and not have to handle a new one for your website. That way, they can focus on maintaining a strong and secure credential including a second factor for the original email account.
Where can I learn more?
If you’re not convinced passwordless authentication is the right option, learn more about our full list of benefits or get answers to the frequently asked questions on password alternatives.
4. Large-Scale Breaches
How do large-scale breaches pose a threat?
As we mentioned earlier, a hacker might attempt to crack an individual’s credentials using a brute force attack. However, the real goal is often to gain access to the website’s user database. Once hackers have cracked the master code, they’ll have a list of all your users’ credentials, and as a result, no level of password security will be able to protect your users.
Password breaches are becoming a real concern for businesses and organizations of all sizes. Storing all of your users’ credentials puts you at risk, and simply encrypting the information is often not enough. Instead, developers need to understand that weak internal passwords and improper storage of credentials could make a hacker’s job easier.
Additionally, the password breaches of other websites could affect your website’s security. Think about it: if you’re using a service from a company that recently had a password breach, your own employees’ accounts could be compromised, which means your end users are also at risk. Once a big company gets hacked, the consequences can start to trickle down fairly quickly.
How can I secure against large-scale breaches?
If your organization continues to use passwords as a user authentication method, it’s important that you store your passwords with more than just encryption. In fact, you can boost your website’s overall security by:
- Hashing your passwords. Hashing your passwords translates them into a random set of characters. Once the data has been hashed, it’s extremely difficult to decode the information without the key. This is especially useful for passwords because they don’t need to be read back. When users log in, the same hashing will be applied and then compared to the information on file.
- Salting your passwords. This technique adds an extra value at the end of your passwords so that it’s harder to determine what the actual credential is. For instance, the password “admin” would change to “admin+salt” when salt is added. For an additional security precaution, the salt added to each password should be random and unique.
Generally, salting occurs after a password has been hashed, meaning that the two processes often work together to ensure additional layers of security. By both salting and hashing your passwords, you’re adding new protections to your database, which makes deciphering the data and gaining access to user information harder to achieve.
However, it’s important to recognize that as our password- based technology improves, cybercriminals’ tools are often trailing not far behind. In fact, some hackers have figured out how to run brute-force attacks on passwords even after they’ve been salted and hashed!
Where can I learn more?
For more ways to protect your users’ sensitive information, check out our top tips for preventing a large-scale password breach on your website.
As you can see, password authentication has many weaknesses that can put you and your users’ sensitive information at risk. Hopefully, this article has made you more aware of password weaknesses and ways you can improve your website’s vulnerabilities. Don’t wait to make changes until it’s too late!
To see more solutions for upping your password security, check out these additional resources:
- A Modern Password: 6 Top Tips for A Secure Login Process. Passwords aren’t the best form of authentication, but they’re still everywhere we look. Read through these tips for ensuring your passwords (and your users’ passwords) are as secure as they can be.
- 6 Must-Have WordPress Login Plugins [Rated and Reviewed!] There’s no need to go re-inventing the wheel when top developers have already created strategic and effective ways to improve your login process on any WordPress site. Take a look at our top suggestions with this guide.
- How Does Two Factor Authentication Work? Steps & Examples. Multi-factor authentication systems place an additional layer of security on what might otherwise have been a weak system. Find out how to implement the protocol on your own site.