At Swoop, we make two-factor authentication simple. It shouldn’t be a hassle for your users to be safe, and it shouldn’t be expensive or complicated for you to keep them safe.
We’ve already walked through the big picture of two-factor in this quick guide – why it’s important, the benefits it has, and different types of solutions.
But if you’re not sure exactly how the two-factor process works, you probably want a deeper understanding of it before installing a new tool on your site. Here’s how the two-factor authentication process works and different examples of two-factor in action.
How does two-factor authentication work?
Here’s a simple way of explaining the two-factor process: asking users to both know something and have something before they’re allowed in or authenticated to use your site. Sometimes sites also require that you be something, usually meaning you’ll use your fingerprint to unlock something.
The idea is that whatever factors the site asks you for will match what the site’s server has on record for you as a user.
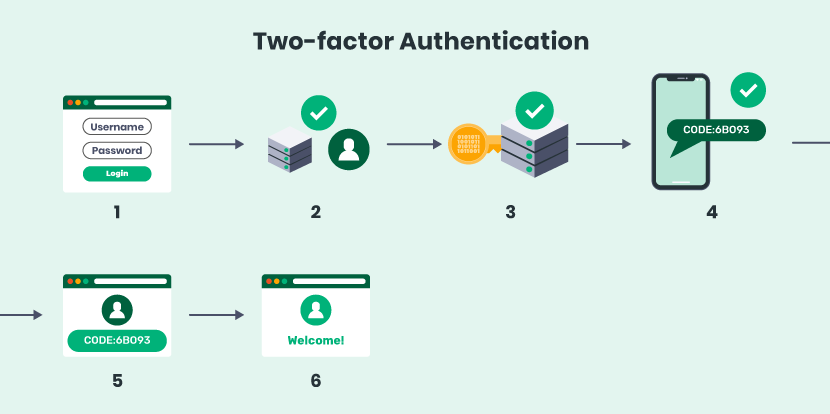
Here’s how the process breaks down step-by-step:
- The user is prompted by the site or app to log in.
- The user enters what they know. This is usually a traditional username and password combo. The site’s server finds a match and recognizes the user.
- For processes with passwordless login options, the site generates a unique security key for the user. The key gets processed by Swoop and validated by the site’s server. Learn more about this process here.
- Next, the site prompts the user to initiate the second step to log in. This step can take a few different forms, but the idea is to prove that you have something only you would have, like your cellphone.
- The user then enters a one-time code that was generated for them during Step 4.
- After going through both factors, the user is authenticated and granted access to the website or app.
Say Goodbye to Passwords
and
Hello to Secure Logins.
Go passwordless and delight your users with secure and seamless one-click login.
Why should you care about two-factor?
A couple of reasons:
First, if you run an online business and don’t take steps to secure your users’ data (beyond a basic password system), you’re putting your customers at risk. There’s really no excuse these days for poor security, with so many tools available and so much at risk.
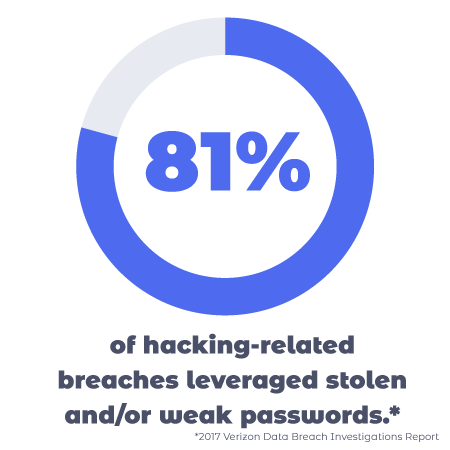
Next, single-factor login is not secure at all. Passwords alone are not strong enough to protect a site. Just think about how many times you’ve reused an old password to make it easier to remember. The internet is full of these human-made weaknesses that are so easy for hackers to tap into. In fact, a Verizon cybersecurity study has found that 81% of all hacking activities start via stolen or weak passwords.
Finally, traditional authentication methods suck for users. Password-based systems ruin the UX value of your site, driving away visitors and new customers. Two-factor authentication is a great way to incorporate new tools and innovations into your site’s login process, like Swoop.
Just make sure your new two-factor tools don’t end making the login process even slower or more complicated!
The bottom line: Any site or app that handles sensitive information has to protect its users. If you rely on your site to convert new customers, an old fashioned login system is even more of a liability.
Two-Factor Authentication Examples
Let’s walk through three of the main forms of two-factor authentication: passwordless, SMS-based, and app-based.
Passwordless Two-Factor Authentication from Swoop
You know: your Swoop PIN
You have: an email address
Swoop is a powerful authentication tool that can completely eliminate passwords on your site. Using ultra-secure email-based authentication techniques, Swoop is basically like generating a brand new password every time you log in and then immediately destroying it once you’re done.
The main idea is that Swoop can be implemented into any combination of authentication factors. You can create your own passwordless two-factor authentication method for your site or app while seriously improving security and UX.
Swoop users have reported the only hard part of installing it is figuring out how to remove the old two-factor solution that wasn’t cutting it.
What’s the best combination of factors for your two-factor authentication system? A Swoop login button + a PIN. Simple, secure, and fast as hell. Plus, it’s extremely cost-effective for small businesses, just a penny a login.
SMS-Based Two-Factor Authentication
You know: your username and password
You have: the special one-time code texted to your phone
This example of two-factor authentication is currently the most common method on the internet. A user enters their password and is then prompted to request a code be texted to the phone number that the site already has on record for their account. Once they enter that code, they’re granted access.
SMS-based two-factor is used by all kinds of sites and services. A typical example might be banks and financial services that let customers manage their finances online.
This two-factor authentication method can also be useful when adapted in other ways. For instance, a one-time SMS code can be used to re-verify your identity if you forget which password you need for a site.
Drawbacks of this two-factor authentication example:
- It can become extremely expensive for online businesses to use, especially for small businesses. Authenticator services typically charge around $.75 per text message. Let’s say you get around 5,000 logins a month. That’s a $3,750 bill for your small business to pay.
- Phones are much less secure than they used to be. Smartphones and phone numbers can easily be hacked or stolen. This would grant a thief access to all your accounts if your phone automatically remembers and fills those passwords.
- Requiring a user to use multiple devices or switch applications is bad UX design. This method isn’t the very worst for UX, but it’s still never a good idea to slow down users trying to interact with your site.
App-Based Two-Factor Authentication
You know: your username and password
You have: access to an authenticator app on your smartphone
This example of two-factor authentication works similar to the first, with an authenticator app directly installed on your smartphone generating the one-time code instead of the online service.
A user enters their password, and then they request a code from the authenticator app. They re-enter this code on the website’s login page, and then they’re fully authenticated.
This two-factor method is often used by web-based apps and suites of tools. Universities, for example, often use authenticator apps to help secure all the different online portals they manage. When used for a suite of apps or services, this method works similarly to single sign-on authentication.
Drawbacks of this two-factor authentication example:
- App-based authentication has security issues just like SMS-based two-factor. Smartphones can be stolen and hacked like any other computer.
- This method creates an awful experience for the user. Like seriously bad. Unless a user already happens to regularly use this method, you’re forcing them to take on all kinds of extra hassles. It ruins your ability to grow your audience.

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
Notice anything different between the two-factor authentication examples?
Swoop is the only secure, easy-to-use two-factor solution that doesn’t require a password.
It’s important to secure your users’ data. Your site flat-out won’t be able to attract and keep an audience otherwise. You need some form of two-factor authentication on your site, but an ideal solution will also improve the user experience.