If your company or organization is looking into stronger security options for your website or application, you’ve probably heard of security authentication and authorization. While these terms are often used interchangeably, they are actually quite different. Understanding the key differences in security authentication vs. authorization is essential for providing top-notch user experiences for each.
Authentication and authorization both play important roles in online security systems. They confirm the identity of the user and grant access to your website or application. It’s vital that you make note of their differences so you can determine which combination of web tools best suit your security needs.
To better understand the relationship, it might help to think of the two terms in this way: authentication asks “Who are you?”, and authorization asks “What are you allowed to do?”
To help you better understand how authentication and authorization work, we’ll walk through each of these key concepts:
- What is authentication?
- What is authorization?
- Security authentication vs. authorization
- Boosting security authentication and authorization
Whether you want to remove the hassle of traditional password logins or implement more rigorous security checks, reviewing these ideas will give you a stronger all-around understanding of online security and how it can be improved. Before explaining how the two processes work together, let’s first discuss what sets them apart.

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
1. What is authentication?
To put it simply, authentication is the process that confirms a user’s identity and provides access to sensitive information.
Traditionally, this is done through a username and password. The user enters their username, which allows the system to confirm their identity. This system relies on the fact that (hopefully) only the user and the server know the password.
The website authentication process works by comparing the user’s credentials with the ones on file. If a match is found, the authentication process is complete, and the individual can be pushed through to the authorization process.
Types of authentication
While password authentication is the most common way to confirm a user’s identity, it isn’t even close to the most effective or secure method.
Think about it: anyone with your credentials could access your account without your permission, and the system wouldn’t stop them. Most passwords are weak, and hacking techniques can break them in less and less time.
Luckily, passwords aren’t the only way to authenticate your users. That’s why we’ll cover two alternative methods that sites can use to verify a user’s identity.
Biometric Authentication
Biometric authentication includes any method that requires a user’s biological characteristics to verify their identity. While this may seem like new-age technology, you’re probably been using it to unlock the screen on your smartphone for years. Fingerprint scanning is the most well-known form of biometric authentication, but facial recognition tools are an increasingly popular choice for developers and users alike.
Of course, hackers have a much more difficult time replicating a users’ biological characteristics than typical password-based methods of authentication. However, it’s important to note that these processes are often less secure than you might initially assume.
For example, small fingerprint scanners on smartphones only record portions of your fingerprint. Multiple images of part of a fingerprint are much less secure than a single, clear image. Plus, some hackers have created a “master fingerprint” that contains characteristics of most common prints, allowing them to trick the scanners.
Remember, too, that biometric authentication can’t be changed or altered if a user’s fingerprints have been compromised. While biometric authentication holds a lot of promise, it’s really most useful as a second factor in a multi-factor authentication strategy.
Email Authentication
Email authentication is a passwordless option that allows users to securely log in to any account using just an email address. The process is very similar to signing in with a Facebook or Twitter account, but this method offers a more universal approach. After all, the vast majority of individuals in the U.S. have at least one email address.
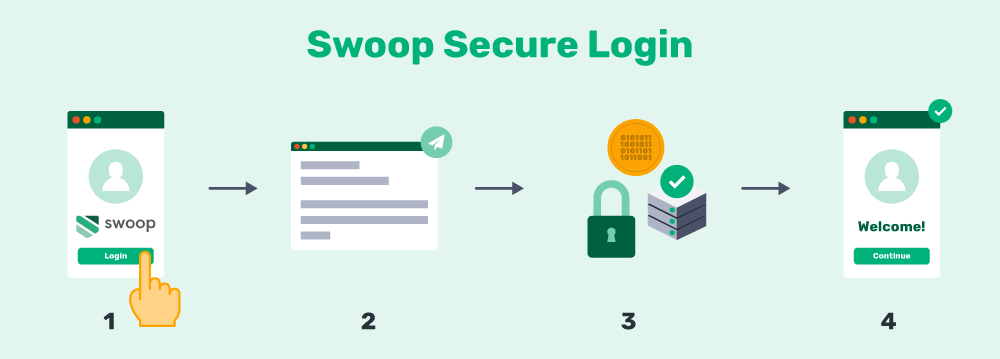
Here’s how your site can authenticate users using Swoop’s Magic Message passwordless authentication:
- The user is redirected to the Swoop service via the OAuth 2.0 protocol for authentication.
- From a browser window, the user pushes the “Send Magic Message” button: The button activates a mailto link, which generates a pre-written email for the user to send.
- The user sends the email: This is where the magic happens. Once the email is sent, the outgoing email server generates and embeds a 1024/2048 bit, fully encrypted digital key into the header of the email. Swoop’s authentication server follows the public key cryptographic procedure to decrypt this key. Each email sent receives a unique key for that message. The level of security for these encrypted keys is beyond comparison to traditional passwords.
- The user is logged into their account: When the key decrypts and passes all layers of verification, the Swoop authentication server directs the website to open the user’s account and begin a session. This all takes place in a matter of seconds and makes for an extremely streamlined user experience.
Aside from being inherently more secure than a password, email authentication tools like Swoop will also provide a more efficient and elegant user experience which has helped increase new signups by up to 49%.
That way, users know their data is protected, and you can avoid any potential breaches in security. It’s a win-win for users and developers alike!
Say Goodbye to Passwords
and
Hello to Secure Logins.
Go passwordless and delight your users with secure and seamless one-click login.
2. What is authorization?
Authorization is the next step in the login process, which determines what a user is able to do and see on your website. Once a user’s identity has been verified through the authentication process, authorization determines what permissions they have.
Permissions are what the user is able to do and see on your website or server. Without them, every user would have the same abilities and access to the same information (including the sensitive data that belongs to another user). Permissions are crucial for a few a reasons:
They prevent a user from accessing an account that isn’t theirs.
Imagine if your online banking application didn’t have permissions. When you logged in, you’d not only have access to your account but also every other user’s account on the application! Permissions ensure users can access and modify only what they need to.
They restrict free accounts from getting premium features.
Let’s say your website offers different feature packages. To restrict free accounts from gaining access to your premium features, you need to implement specific permissions so that each account only has access to the capabilities they paid for.
They ensure internal accounts only have access to what they need.
Your users aren’t the only ones that need permissions— your staff accounts need them, too. Staff may have access to higher levels of data than the average users, but it’s crucial to set restrictions for them as well. For example, users’ contact information might be useful for your marketing team, but they should never be able to access your users’ more private credentials.
Ensuring effective authorization and permission settings are essential for any website or application. In fact, setting the right permissions is just as important as using a secure authentication method.
Without dictating what users can see and do, your information is no safer than if there were no first layer of authentication at all. And while strategic authentication methods only require that a user verifies their identity a single time per session, authorization occurs with every request the user makes— starting with the initial login process.
3. Security authentication vs. authorization
Authentication and authorization are often discussed in tandem. However, it’s important to recognize key distinctions between the two. In the login process as a whole, one step can’t be completed without the other. Still, authentication must always come first.
How are authentication and authorization different?
The easiest way to understand this relationship is by asking yourself the questions, “Who are you?” and “What are you allowed to do?”
Just like it would be impossible to determine what an individual is allowed to do if you’re not sure who they are, your registration and login systems cannot authorize users if they’ve yet to be authenticated.

In other words, authentication identifies users while authorization determines their permissions. While they’re entirely different processes, they work together to ensure a seamless login experience for users— and neither one can be completed without the other!
How do authentication and authorization work together?
Security authentication and authorization should be incorporated into any website or application, although it’s especially vital for those that process online transactions or personal information.
Since anyone with the “key” can gain access, it’s vital that companies implement a strong authentication strategy to keep unauthorized users from accessing accounts without permission.
4. Boosting security authentication and authorization
Authentication and authorization keep internal accounts organized and help catch unauthorized activity before it becomes a serious threat. One of the main steps we recommend to protect against breaches is to make sure every account has only the permissions they need. That way, your team can spot any unusual behavior early on and take the necessary steps to correct or shut it down.
Strong security authentication protocols prevent cybercriminals from gaining access to your accounts. Having a secure authentication method will make it more difficult for hackers to crack a users’ key and gain access to their information.
The only surefire way to completely prevent that kind of breach? Remove hackable keys from the equation entirely. All companies and websites should consider incorporating one or more password alternatives to replace a traditional username/password authentication system— like Swoop’s magic email authentication!
Hopefully, this guide has helped you understand the differences between security authentication and authorization. Now you’re all set to look into web security options with a better understanding of how your users are protected— and why some security measures are more important than others.
For more information on security authentication and authorization processes, check out these additional resources:
- Using Token-Based Authentication to Improve Your Website: One way to improve the usability and security of a website is to implement token-based authentication. Find out how with our comprehensive guide.
- 6 Shocking Reasons Why Passwords Won’t Protect Your Website: Passwords are the most common website authentication method, but they’re also the least effective. Learn more about why passwords aren’t the best way to protect your website or your users.
- A Definitive Guide to Two-Factor Authentication: Two-factor authentication is a common way to boost web security levels. Read more about the benefits and how to implement it on your own website with this guide.