When it comes to online security, one of the worst things to happen is when a hacker gains access to your email account. Aside from it just being a hassle—you have to change your password or create an entirely new email address—hackers can use the information from your email to enter other accounts with even more sensitive data.
Think about it: a common way to reset a password once it’s been forgotten is to send it through your email address. This means that a hacker could potentially gain access to anything from your Netflix account to your online banking account.
Even organizations should be cautious of their employees’ email accounts. With access to an employee email account, hackers could cause real damage to your organization’s website and obtain sensitive information from your user database.
Luckily for websites and users, there are ways to protect email addresses from cybercriminals.
We’ll cover eight ways users and websites can protect their information:
A. Email Password Breach Prevention Tips for Websites
- Implement a secure login process
- Use emails with end-to-end encryption
- Protect and secure your administrator accounts
- Train employees on security best practices
B. Email Password Breach Prevention Tips for Users
- Create strong passwords for all email accounts
- Set up two-factor authentication
- Check your email’s recent account activity
- Only create accounts on websites you trust
Let’s dive into the first tip!
Email Password Breach Prevention Tips for Websites
Email Password Breach Tip #1: Implement a Secure Login Process
Your organization’s main objective should be protecting your users’ information, and one way to achieve this is by implementing a secure login process—both internally for employees and externally for users.
You might be thinking “We already have a secure login process,” but odds are you could do more to improve it.
Traditionally, you enter a password and username to confirm your identity before you can access your account.
In theory, this step stops unauthorized users from gaining access, but the truth is most accounts aren’t secure because their passwords aren’t strong enough.
Nowadays, it’s easy for a hacker to guess a user’s password or obtain it through a brute-force attack (which means that software is used to run through every possible combination until a match is found).
What’s more? People aren’t using password security best practices to create strong passwords.
If passwords can’t be trusted to protect your website’s information, what can you use?
Tech-savvy websites are gravitating toward more secure options, such as:
- Email authentication. Instead of creating an account or logging in with a password, users can access information by verifying their email address.
- Token authentication. Using a physical token or a single-use passcode that is sent to your phone via text, users can access their accounts without having to create or remember their own passwords.
- Biometrics. Everything from fingerprint and facial scanning to voice analysis falls under the category of biometrics.
Swoop’s secure email authentication tool, for example, uses three layers of security checks to determine if the request came from an authorized user. If our system suspects that any suspicious behavior like a login request made from an unidentified device, users will be asked to confirm or decline their request via text message.
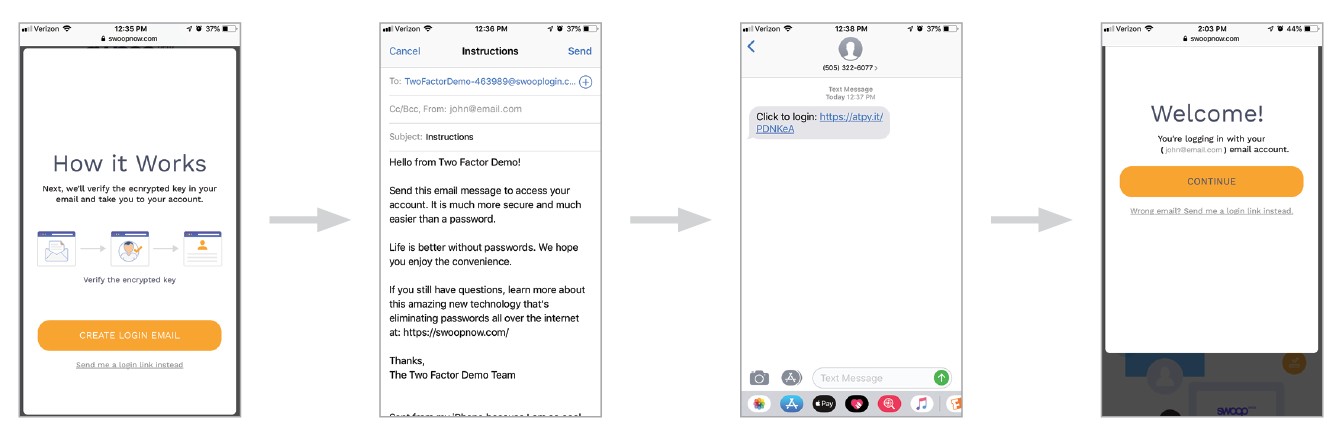
That way, if a user does experience an email password breach, the accounts linked to the email address won’t be compromised.
Key point: Organizations shouldn’t rely on passwords to protect their users’ information. By utilizing a passwordless login option, a user’s other online accounts can still stay secure even if his or her email address becomes compromised.
Email Password Breach Tip #2: Use Emails With End-to-End Encryption
We’ve talked about how you can protect your users’ accounts, now it’s time to look at how you can secure your employees’ emails.
Depending on the nature of your organization, you could be sending emails with sensitive information.
One of the biggest concerns with internal account security is that employees are sharing their account credentials via email. In fact, 1 in 7 employees share passwords with other team members. With credentials stored in your employees’ inboxes, it makes the hacker’s job easier.
If a hacker gains access to one email account, he could obtain the credentials of another account with higher permissions and cause further damage from there.
If a hacker can’t access an employee’s email account, he might try to gain access to your email server to obtain the content from your company’s emails.
Organizations can protect themselves from this type of threat by using end-to-end encryption.
Unlike regular encryption, with end-to-end encryption the key to decrypt messages isn’t stored in the server but rather in the client systems. This way, if a hacker does access your email server, there’s no way for him to decrypt the emails.
Another benefit of end-to-end encryption is that each client system as their own key. If a employee device is compromised only one key is lost which means that the entire system isn’t compromised as a result.
Say Goodbye to Passwords
and
Hello to Secure Logins.
Go passwordless and delight your users with secure and seamless one-click login.
Organizations have two solutions if they want to implement end-to-end encryption:
- Train employees on how to use an email encryption system.
- Use a secure email provider that has an email encryption system built-in like ProtonMail, Hushmail, or Tutanota.
Even with proper security training, it’s impossible to stop every employee from sharing credentials, but with end-to-end encryption, you’ll make it harder for hackers to access the information.
Key point: Protecting your employees’ email accounts should be about more than just securing their credentials. Organizations need to use end-to-end encryption to secure the information being shared via email as well.
Email Password Breach Tip #3: Protect and Secure Your Administrator Accounts
When cybercriminals hack into an employee’s email account, their goal is to find a way to access an administrator account. These accounts have the highest permissions that can change the settings of other accounts and, generally, have access to sensitive information.
That’s why it’s important for organizations to take extra security measures to protect their administrator accounts.
Organizations can use the following best practices to ensure their administrator accounts stay protected:
- Ensure that credentials for administrator accounts are never shared. As we mentioned in the last section, sharing credentials via email can be risky, especially if you’re not using end-to-end encryption.
- Each administrator role should have their own credentials. Having one set of credentials that’s used among every administrator means you can’t track what changes came from which user. Additionally, since everyone is using the same credentials suspicious behavior can go unchecked because employees may assume that the changes where made by another team member.
- Logging into an administrator account should only be done on a secure computer. This acts as another precaution to ensure that your admin credentials stay protected and out of unauthorized users’ hands.
It’s also important to limit the permissions every account has to what’s necessary for their role. If every employee had an account with the same permissions as an administrator, a hacker could breach any account and start making changes.
To learn more about protecting your administrator account, check out Swoop’s article on data breach tips.
Key point: Protecting your administrator accounts will make it more difficult for hackers to access high-level permissions to your organization’s website or user database.
Email Password Breach Tip #4: Train Employees on Security Best Practices

Last, but certainly not least, it’s crucial that you get your organization’s employees on board with your security plan.
While your employees may have been trained on security best practices when they started working for your company, it’s likely that those strategies have changed or evolved. Additionally, employees not only need to know what they should do but also why it’s important.
Think about it this way: employees are less likely to follow your instructions if you tell them they have to create stronger passwords.
In contrast, when you tell them that stronger passwords make it more challenging for hackers to gain access to their email accounts (which can prevent information from getting leaked), they’ll be much more willing to comply.
When you train your employees on email and account security, make sure to include:
- The steps your organization is taking to implement better security.
- Ways employees can protect their accounts.
- Next steps if they suspect their account has been compromised.
It’s important that you have these training sessions whenever updates are made. That way, you and your employees stay on the same page and security best practices stay fresh in your employees’ minds.
Key point: Training employees should be a part of any organization’s security plan. When your staff knows how to effectively protect their email accounts and what to do if their accounts become compromised, you’ll be able to catch hackers before they cause any real damage.
Email Password Breach Prevention Tips for Users
Email Password Breach Tip #1: Create Strong Passwords for All Email Accounts
We can’t stress it enough: passwords can be easily cracked, especially when users aren’t following password security best practices.
By using the following strategies for all your email accounts, you can better protect your sensitive information:

It’s also important that users create a different password for every account. With so many accounts to juggle, 54% of people use 5 or fewer passwords across all of their accounts.
While using the same or similar passwords for every account may make it easier for you to manage, it makes the hacker’s job easier, too.
When a hacker cracks your email account, the first trick they’ll use to access another account will be entering your email address and the compromised password. If the two match, the hacker will have entered another one of your accounts. This process can lead to a domino effect that leaves all of your online data at risk.
With separate equally strong passwords on all of your accounts, there’s less chance of a hacker compromising multiple accounts.
Key point: Passwords are still widely used as a secure authentication method, so it’s vital that users know how to create strong passwords for their email accounts.
Email Password Breach Tip #2: Set Up Two-Factor Authentication
Nowadays, most email providers offer users the option to enable two-factor authentication. While it’s another step you have to take in the login process, it can protect your email accounts from getting hacked even if an unauthorized user has your credentials.
Swoop has an in-depth look at two-factor authentication, but the simple version is that users have to verify their identities using two authentication methods.
Here’s how the process generally looks:
- After users sign in with their username and password, they’ll be sent a single-use passcode to the phone number on file.
- Users will have to enter the code on the login screen before they can access their account.
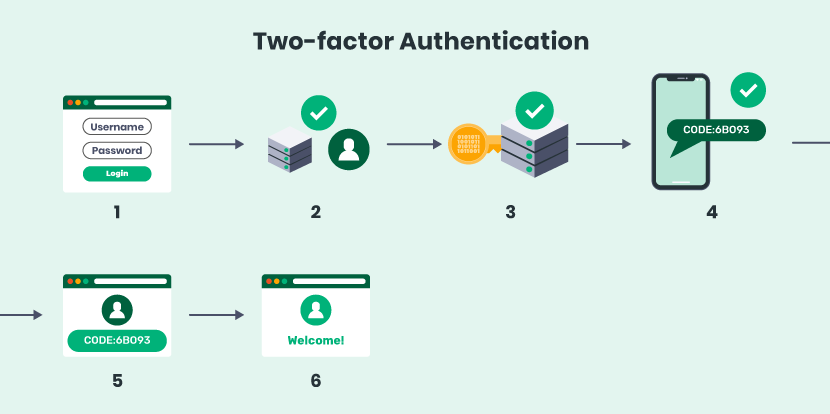
Keep in mind: some email providers will only require this step if you’re attempting to log in on an unfamiliar device or the system suspects suspicious behavior.
This extra step ensures that users are who they say they are. Since it would be very difficult for a hacker to obtain your phone, this can prevent your account from becoming compromised even if your credentials are hacked.
Additionally, this step can help you identify when a hacker has tried to access your account. For example, if you receive a passcode that you didn’t request, you can change your password to further deter hackers from trying to access your email.
In order to set up two-factor authentication, you have to go to your email account settings, add your phone number, and enable the feature.
Key point: Two-factor authentication is like your account’s security failsafe. Once enabled, hackers won’t be able to access your account unless they have the passcode that’s sent to your phone.
Email Password Breach Tip #3: Check Your Email’s Recent Account Activity
Preventing your email from getting hacked is only half the battle. It’s also important for users to be able to spot if their accounts have already been compromised so that they can take the necessary steps to secure their accounts again.
One way to check if your account hasn’t been tampered with is by looking at your email account’s recent activity.
Many large email providers (like Gmail and Outlook) allow you to see when you’ve logged in, including information like:
- Location
- IP address
- Date and time
- Login type (i.e. browser, authorized application, etc.)
By checking this information on a regular basis, you can spot any unusual activity and stop it before the hacker gains access to any of your other accounts.
When you look at the information, make sure that:
- The login types are from your web browsers or authorized applications.
- The locations look familiar (generally, anything outside the United States should be a red flag).
- The login times and dates reflect when you most recently accessed your account.
Users are able to access their account activity in their email’s settings, so make a point to check it on a regular basis.
Key point: Users should take the time to review their email activity as a way to spot any suspicious behavior early.
Email Password Breach Tip #4: Only Create Accounts on Websites You Trust Are Secure
There are two ways hackers can gain access to your email account:
- By cracking or guessing your account credentials.
- By hacking into the website’s user database where your credentials are stored.
Most hackers prefer the second option because it means they won’t have access to just your credentials but everyone else that has an account on the website. Moreover, in the case of a user data breach, even a strong password won’t be effective because the hacker will have a list of everyone’s credentials.
That’s why just protecting your account might not be enough to stop your email from becoming compromised. As such, users need to pay close attention to the types of websites they create accounts on.

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
A secure website is using the best practices we mentioned above and other methods to ensure that a user data breach doesn’t occur.
Only create accounts on websites that you trust are secure and be cautious of the type of information you disclose. For example, if you have an account on a website you don’t fully trust, don’t keep your contact or payment information on file and ensure that you’re using a strong password.
Additionally, gravitate toward websites that use passwordless login options, as this type of website authentication is more secure and harder for hackers to crack.
While some data breaches can’t be avoided (even with websites that do take extra security precautions), it’s better to be safe than sorry. Plus, only creating accounts on websites you trust will minimize the number of credentials you have to manage.
Key point: Take extra care to only create accounts using secure, trusted websites so that you can rest assured knowing they’re protecting your sensitive information just as much as you are.
Whether you’re an organization looking to improve your website’s security or a user trying to implement secure best practices, these tips can help you stay protected online.
Your email could hold a lot of sensitive information as well as become the gateway for hackers to access your other accounts. With these eight tips, you can avoid an email password breach.
For more information about protecting your online accounts, check out these additional resources:
- Are Your Passwords Compromised? Why Companies Are at Risk. Because companies store sensitive information on all of their users, they are the most likely victims of a password breach. Learn more about how passwords could be making your website insecure.
- Understanding User Authentication: 3 Basics You Should Know. User authentication is the process websites use to verify the identify of their users. Learn more about the ins and outs of this vital part of your website security.
- 4 Password Authentication Vulnerabilities & How to Avoid Them. Learn more ways you can protect your users’ sensitive information by exploring password’s vulnerabilities.