Your company is ready to begin development for a new web application. That’s great! But before you begin the process, do you have a plan to ensure your application is as secure as it can be? Or perhaps you already have a live web application and you’re looking to implement strengthened security measures.
Protecting sensitive information within your application should be a top priority, especially with the increase in data breaches at large companies. You don’t want to put your users at risk because it could cause them to lose trust in your organization and potentially leave you legally liable.
We want your application to succeed. That’s why we’ve compiled a list of best practices for web application authentication to boost your security and maintain your users’ trust:
- Create a web application authentication checklist.
- Explore various web application authentication methods.
- Store sensitive data separate from regular data.
- Test your process with low-privileged accounts.
- Use a firewall to boost your web application authentication.
These tips are focused on securing internal accounts to ensure hackers can’t access admin-level permissions. However, many of these best practices can be used to secure your users’ accounts as well.
What’s more, your application doesn’t have to be in the developing stages to implement these tips. In fact, companies should make it a practice to conduct regular web application security checks, and these top tips can help!
Let’s get started.
1. Create a web application authentication checklist.
Securing your web application can seem like a never ending task, and we understand a lot goes into keeping your sensitive information protected. However time-consuming the process may seem, it still needs to be done— especially when around 90% of user-generated passwords are vulnerable to hacking.
If you’re not sure where to get started, the best place to begin is by creating a checklist that details the steps you’ll take to ultimately reach a secure web application.
Your checklist should include these four key steps:
Step 1. Gathering Information
The first step in creating a highly secure web application authentication process is to gain a better sense of any third-party applications your organization uses. Take note of what information is stored in those applications and how information is transferred between your application and the others apps your company uses. Even if your application is secure, the other applications your company uses could put you at risk if they aren’t secured as well.
Start by pointing out areas in each platform that might be at risk and determine which areas of the application can be tested, whether manually or by using a security tool.
Once you’ve outlined the applications you need to test in addition to your own and pinpointed potential vulnerabilities, you’re ready to move to the next step.
Step 2. Planning a Course of Action
At this stage, you’ll document your testing strategy and define the types of risks each application presents. For instance, if an application has an authentication component, you should check for password complexity guidelines and vulnerability to brute-force attacks, among other security factors.
Make sure everyone on your IT team knows what tasks they are responsible for and create a timeline for when the testing will be completed. For example, one team member could be assigned to test the security of your marketing software, while another tests your internal communication tools.
Once your plan is all ironed out and tasks are delegated to the right team members, you’re ready to move to the next step.

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
Step 3. Executing Your Security Checks
Next, it’s time to execute your security checks. It’s likely that each application you test will require a combination of automated and manual checks to ensure everything is in order.
Your manual tests should cover common vulnerabilities. In most cases, the tester will act as if they’re trying to hack into the website to identify areas that are defenseless. Automated security checks, on the other hand, utilize computer programs to locate more obscure vulnerabilities. A machine can quickly scan through your application to pinpoint risks, but they often lack the ability to spot logical flaws. By combining the two processes, you’ll likely be able to discover most, if not all potential liabilities.
Once all security risks have been identified and a thorough report has been created to identify the most pressing security concerns, you’re ready to move to the next step.
Step 4. Remedying Major Problems
Now that you’ve discovered your application’s major risks — whether they be external or internal — you need to classify each problem and determine where the risk originated from. After all, it’s hard to find a solution if you’re unable to locate the root of the problem!
For example, here are three main categories of security risks along with suggested fixes:
- App-related risks might require updates to your application.
- User-generated risks could mean you need more intensive staff security training.
- Third-party application risks may require that you transition to a more secure alternative.
Bottom line: Once you’ve categorized each risk, determined an appropriate solution, and implemented the changes, your web application authentication process will be significantly more secure.
2. Explore various web application authentication methods.
Password-based login systems are still the most-used form of web application authentication but are also a highly insecure one which will add an increased burden on the application developer. More than likely, your application requires some sort of username and password combination to verify a user’s identity and grant access to restricted data.
Not to mention the authentication systems for various third-party applications used by your team members! That can be a lot of passwords to remember.
However, it’s important to remember that security experts believe passwords aren’t the best defense against unauthorized activity. That’s because:
- They’re easy to guess manually or using automated tools.
- User-generated passwords often follow a pattern, which makes them easier to compromise.
- The same credentials are typically used to protect multiple accounts.
- Passwords aren’t always stored in the correct way.
So what can you do to negate these concerns and ensure a top-notch authentication system for your application? Here are our two main suggestions:
Strengthen password standards.
As you develop (or update) your web application, you’ll want to make sure your password standards are up-to-par. That means not allowing users to create some of the most common and easily hackable passwords, and instead prompting them to select a stronger alternative. Take a look at these suggested “do’s” and “don’ts” to help inform your own standards:

Even with top-notch standards implemented throughout your web application, passwords are still not the most secure option. Plus, maintaining regularly updated password standards can take a toll on the developer, whose time can be better spent elsewhere— which leads us to our next suggestion!
Consider passwordless alternatives.
The existence of passwords will always bring with it a relatively easy opening for hackers. That’s why we recommend using passwordless login alternatives within your application. This way, both staff and users will have one less password to manage, and hackers will have one less “in.” Instead, users can verify their identities using one of the following:
Passwordless authentication is significantly more secure than traditional password-based login tools. Instead of relying on a simple, user-generated string of characters, password alternatives typically require users to verify their identity using a biometric characteristic or possession factor, such as an email address, to be authenticated. After all, these alternatives are much harder to imitate as a scammer, making alternative web application authentication methods stronger than their traditional counterparts.
Swoop’s login tool, for example, runs email addresses through three layers of security checks to ensure that the email came from the intended user.
Passwordless authentication seems great, right? So what’s stopping you from completely obliterating passwords from your application?

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
While you’re likely able to implement passwordless login into your own application, it might not be a possibility with the other applications your company uses. After all, the third-party app builders must first decide to integrate passwordless alternatives into their system before users, like you and your team, can take advantage.
Since any account linked to your application (like your constituent database) could put you and your users at risk, make use of these best practices to help ensure that your remaining passwords are strong enough to prevent a data breach.
Bottom line: Despite their vulnerabilities, passwords are often the only defense against hackers trying to access your sensitive information. If you can’t use a passwordless option, make sure your credentials are strong enough to deter unauthorized activity.
3. Store sensitive data separate from regular data.
A common mistake that many web and app designers make is that all data is stored together in one large, often encrypted, file. However, when the entirety of your user and internal information is together, it’s difficult to give accounts the right permissions to access the data.
For example, your marketing and outreach department might need access to your users’ contact information, but they shouldn’t have access to anyone’s username or password. To better understand the relationship between authentication and permissions, check out this helpful guide.
Many security experts suggest classifying information into three categories:
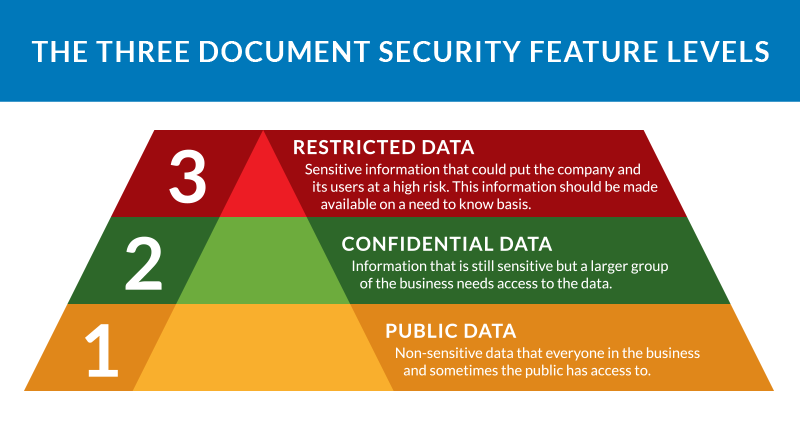
- Public data: Public data is non-sensitive information that presents minimal risk to the business. This information is generally accessible to anyone in the business as well as sometimes publicly displayed, like a person’s first name on their social media account.
- Confidential data: Confidential data is information that is sensitive but still needs to be accessed by an entire department. For instance, users’ home addresses should still maintain a level of privacy but may be useful to your marketing team, who will often send out direct mail.
- Restricted data: Finally, any sensitive information that could put the company and its user at high risk should be considered restricted data. This information should only be made available on a need-to-know basis.
With a better sense of how to categorize information, your company can not only determine how you will protect information but also who will have access to the data. If you’re interested in learning more about how to protect your passwords and other sensitive data, check out our list of strategies to prevent a data breach.
Bottom line: Dividing your information based on the level of confidentiality is a web application authentication best practice that will help ensure your sensitive information is only accessed by those who need it.
4. Test your process with low-privileged accounts.
One of the most important parts of our web application authentication checklist is identifying your most significant risks. But how exactly does your company go about finding gaps in your application’s defenses?
Every application has specific permissions for certain accounts or computers. These permissions dictate what a user is able to do and see when they’re on your application— also known as authorization.
For instance, a customer’s permissions will be drastically different than an employee’s. While an employee might be able to modify elements of the application, a customer should only be able to make changes to their own profile.
Ask yourself the following questions to better understand your application’s vulnerabilities and become better equipped to handle any errors that may arise:
- Does our website use passwordless login? If not, are we implementing a form of two-factor authentication to protect accounts that have been compromised?
- Have we limited the number of login attempts to prevent hackers from attempting a brute-force attack?
- If our application allows users to authorize other applications to access information, is the OAuth process secure?
It’s common for hackers to use low-level accounts as an entry point into your application’s infrastructure. This is largely due to the fact that these accounts:
- Are often less secure and use weak passwords.
- May contain higher-level permissions that were never removed or updated.
- Aren’t monitored or maintained as closely as high-level accounts.
That’s why it’s crucial to ensure all new security protocols protect users on the lowest levels and that every account has only the permissions it needs. That way, hackers can’t make significant changes even if they do manage to access a lower-level account.
Once you’ve made sure that lower-level accounts are protected, your team can move on to higher-level accounts to ensure security measures stand strong no matter how many permissions an account has.
Bottom line: Implementing new security protocols is only half the battle; you need to make sure these solutions work for accounts with low- and high-level permissions.
Say Goodbye to Passwords
and
Hello to Secure Logins.
Go passwordless and delight your users with secure and seamless one-click login.
5. Use a firewall to boost your web application authentication.
The last web application authentication best practice we recommend is to use an application firewall during the entire process.
Running your application through tests and implementing changes could take weeks— even months— to get through all the major threats. During that time, your company will be even more vulnerable to attacks.
That’s why it’s vital that your team is vigilant in monitoring your application for any threats— but your staff can’t do it all on their own. We recommend you use a web application firewall (WAF) to further protect your company from any threat that might slip through the cracks.
Essentially, any malicious traffic routed through a WAF is blocked, and you can even create custom rules to further protect your application.
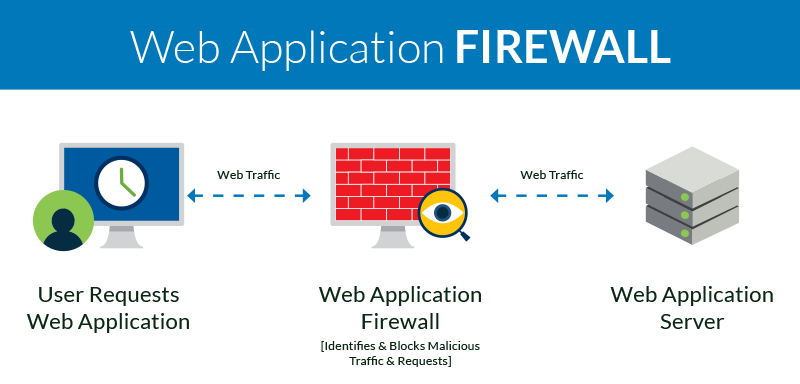
What’s more, a WAF can be in continued use after your security check as an ongoing monitoring system for your company’s application. In addition to the standard monitoring your IT conducts, this will help prevent data breaches and potential attacks. Even simple security plugins for WordPress sites can make a huge difference for your website’s defenses— and they’re easy to implement!
Bottom line: Your application is at its weakest when your team is testing and implementing changes. Create an additional layer of protection by using a web application firewall.
Ensuring high levels of security in your web application authentication system is a never-ending process that requires regular attention and dedication. After all, hackers are only getting smarter— so it’s important that you stay one step ahead!
Hopefully, you’ve learned how to organize the process as well as a few tips and tricks to make the experience go more efficiently. For more information about web authentication and how to protect your application, check out these additional resources:
- Why Your Website Should Utilize Passwordless Authentication: Interested in learning more about why passwordless authentication is the new wave of online security? Check out this list of reasons why password alternatives can be beneficial for your company or organization.
- Top Single Sign-On (SSO) Solutions for Companies and Nonprofits: With SSO, users are able to log into multiple accounts using just one set of credentials. Learn about our top recommendations for a tool that can help your application thrive.
- 6 Ways to Create a Modern Password & Username Login Process: Most common passwords leave users’ accounts open to vulnerabilities. Check out these best practices for strengthened login systems.