Passwords have ruined the Internet.
Think about it. How many online accounts do you have for all the social media, shopping, banking, educational, professional, and entertainment sites you use? Studies show that the average internet user has more than 90 online accounts.
Now consider— If you have a website or online business, do you require users to create accounts with passwords?
If you do, you’re actively driving away customers and visitors. 75% of users quit after a password reset, and 30% of online customers abandon their shopping carts if forced to register with a password. Passwords create a terrible user experience. They drive more business to the internet giants of tech and retail and away from sites and businesses like yours.
You might argue that passwords serve an essential security function. That’s where you’d be wrong. Forcing users to create yet another password simply results in the creation of weaker passwords.
We’ve all done it — reused an extremely simple password over and over for the sake of convenience. Plus, even with a strong password, security isn’t quite as tight as you’d think.
As online consumers, we’re threatened by the shady data practices of companies small and large. As online entrepreneurs, we can’t guarantee the absolute security of our users’ passwords when hacking technologies become more and more advanced every day.
So what’s wrong with passwords?
Put another way: Passwords cause more harm than good in an internet that’s clearly ready to move past them.

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
Luckily, the technology exists to replace passwords with highly secure, lightning-fast encryption techniques while still giving websites the ability to properly authenticate their users. It’s called passwordless login.
We believe that passwordless login systems have the ability to completely change the internet for the better. Sensitive data doesn’t have to be protected behind extremely thin layers of password security. We already have the tools to move beyond this.
Now, chances are you have a few questions. That’s why we’ve gathered some of the most frequently asked questions we receive from developers, bloggers, small business owners, and even consumers. Basically, anyone who’s curious about passwordless login.
Feel free to skip around to the questions that interest you most, or read along with us from the top as we answer some of the questions you may not even know you have:
- What is passwordless login?
- How does passwordless login work?
- What are the main types of passwordless login?
- Are passwordless login systems more secure?
- What are the benefits of passwordless login?
- Are there risks associated with passwordless login?
- How user-friendly is passwordless login?
- Which types of websites can use passwordless login?
- How hard is it to implement passwordless login on my site?
- How do I promote passwordless login to my users?
Obliterating the need for passwords begins with raising awareness and understanding that alternatives to the old way of doing things already exist. Ready to learn more? Let’s dive in!
1. What is passwordless login?
Passwordless login systems are tools that websites can implement so that their users are able to log in without creating and entering a password.
However, this doesn’t mean that users are simply let into the site without any form of identity verification! With any type of passwordless login, users still have to prove that they are who they say they are with one or more forms of authentication (just not a password).
2. How does passwordless login work?
There are many types of passwordless login systems (which we’ll explore in more depth below), each working a little differently.
Essentially, any login process — including passwords — will rely on one of the following characteristics to verify a user’s identity:
- Knowledge factors: A knowledge factor is, understandably, something that the user knows. Ideally, it’s something that only the user knows — meaning that unintended users are denied access when they don’t have the right credential. All password-based login systems utilize this method of authentication, although it’s the least secure of the three.
- Possession factors: A possession factor allows users to verify their identities based on something they have — whether that’s a physical item like a key card or a digital asset like an email account. Using a possession factor as a password alternative works based on the idea that the intended user would be the only person with access to the predetermined asset, thus verifying the user’s identity in the process.
- Inheritance factors: An inheritance factor, when used for authentication purposes, is a physical characteristic of a user that is unique to the individual. For example, each person has a one-of-a-kind fingerprint or iris that can be scanned to verify the user’s identity.
Passwordless login works by utilizing one or more of these factors to verify a user’s identity without a password.
Every authentication method boils down to the user being able to prove that they are who they say they are to a digitized system that then decides whether to grant or deny access. In a perfect world, only the intended user would be able to get in. However, each one of these methods comes with its own set of drawbacks, meaning that no authentication factor is fool-proof.
So how can you make sure to choose the right system for your website? Let’s take a look at some of the top-rated and highly secure options for passwordless login.
3. What are the main types of passwordless login?
Passwordless Email Authentication
As the most promising passwordless authentication method, email-based systems verify a user’s identity using their email address and a complex encrypted key code.
Let’s walk through the process for our very own Magic Message password-free authentication tool:
- The user is redirected to the Swoop service via the OAuth 2.0 protocol for authentication.
- From a browser window, the user pushes the “Send Magic Message” button: The button activates a mailto link, which generates a pre-written email for the user to send.
- The user sends the email: This is where the magic happens. Once the email is sent, the outgoing email server generates and embeds a 1024/2048 bit, fully encrypted digital key into the header of the email. Swoop’s authentication server follows the public key cryptographic procedure to decrypt this key. Each email sent receives a unique key for that message. The level of security for these encrypted keys is beyond comparison to traditional passwords.
- The user is logged into their account: When the key decrypts and passes all layers of verification, the Swoop authentication server directs the website to open the user’s account and begin a session. This all takes place in a matter of seconds and makes for an extremely streamlined user experience.
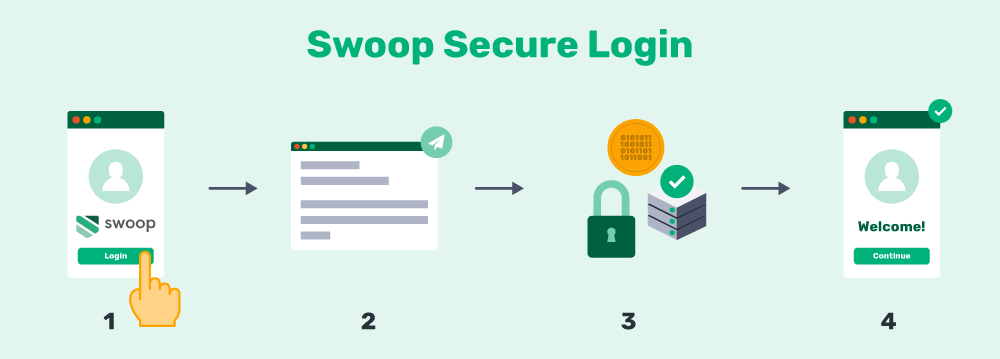
We cover the whole process in greater detail on our How it Works page, but the main point is that email authentication is lightning-fast, ultra-secure, and completely eliminates the need for users to create new passwords.
Passwordless email authentication methods are already becoming popular in certain contexts. One great example: nonprofit pledge giving tools. Nonprofit donations sit at the intersection between the need for tight security and the need for flawless user experience. However, our tools are quickly expanding to reach other contexts as well, including businesses and organizations of all shapes and sizes.
Social Sign-In Authentication
Social sign-in and email authentication operate on similar concepts. With email-based systems, a user’s personal email address is associated with a unique encrypted key as it’s processed through layers of security. With social sign-in, a comparable process occurs through the user’s social media account.
This means it verifies your permissions to view content, make posts, etc. each time you begin a new action. By checking the token’s signature against its security algorithm, the site can effectively verify users’ identity for multiple actions and subdomains, greatly reducing login friction along the way.
Social sign-in authentication is extremely efficient and flexible, but it can be tricky for some sites to implement. Plus, not all users will come to your site ready with a social media profile in hand. Not to mention, many users will be wary (at best) about sharing their sensitive data with a tech giant like Facebook.
Email-based authentication tools work via a similar concept of encrypted keys, so they’re often the fastest way for websites to get started with these innovative login techniques. Plus, almost everyone already has an email account to use!
Biometric Authentication
Growing in popularity is the fingerprint, face, and iris-scanning authentication (also known as biometrics). You might already use a fingerprint or face scanner on your smartphone. You probably don’t think of them in exactly these terms, but they’re a form of passwordless login that the general public is quite familiar with.
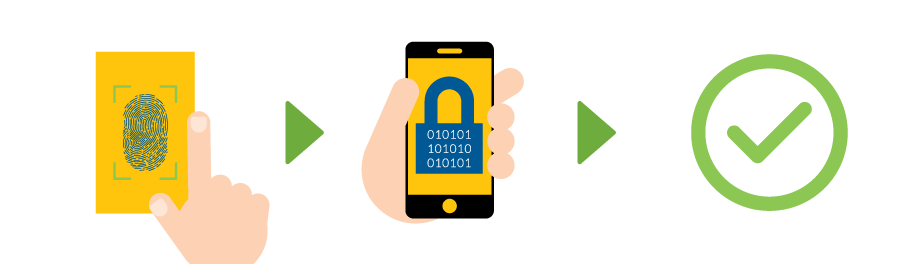
The concept is simple; for fingerprint authentication, users press their thumbs on their phone’s fingerprint reader to authorize payments or gain access to their accounts. While this technique is intuitive and can completely streamline the login process to its core, it does come with some challenges. Namely, accessing technology with a fingerprint reader can be costly for your users, and the technology is less cost-effective for businesses and nonprofits.
Additionally, these technologies have also already been proven to be less secure than expected. For instance, the tiny fingerprint readers in a smartphone can only register parts of a user’s fingerprint. The odds of another person’s finger matching that part of your own print are surprisingly high. Plus, some hackers have created a “master fingerprint” that can bypass nearly any fingerprint scanner.
Biometrics are developing fast, though. A passwordless login system that makes use of encrypted email authentication and a truly secure biometric could completely change the ways in which we engage with the internet via multi-factor authentication.
4. Are passwordless login systems more secure?
We touched on this at the beginning of this article. Are password-based login systems actually insecure? Yes. Are passwordless login systems more secure? Also yes.
While there are tons of ways to actively make your passwords stronger — such as changing them annually, avoiding information that a hacker could easily learn about you, ensuring lengthy passwords with nonnumerical characters, etc. — very few of us actually take these precautions unless forced to.
That’s because we’re either too busy to deal with them or because going through all that trouble for an online account (that might not be particularly important anyway) feels like a huge waste of time.
As a result, many people use the same password or similar variations. This creates a domino effect that allows hackers access to multiple accounts just by cracking a single password.
Passwordless login systems offer a smarter alternative. For example, email authentication allows your new users to register by simply entering their email addresses. They’ll have secure, convenient access to all your content and tools without creating more and more vulnerabilities for you with their weak credentials.
Plus, these systems make use of more advanced authentication methods than traditional username/password systems. They scramble sensitive data and decentralize access using these techniques:
- Tokenization is a form of security that randomly generates a token or a string of characters. This token can be a substitute for the real data and is harder to crack because there is no mathematical relationship between the real data and the token.
- Encryption is very similar to tokenization but uses an algorithm to transform sensitive information into ciphertext. This ciphertext can only be decrypted with the encryption key.
As a website administrator or online entrepreneur, your users’ information could still be at risk even if you institute the tightest of password controls. Even the strongest passwords are still susceptible to constantly evolving hacking technology. Passwords are a glaringly weak link in the entire authentication process. Removing them is the solution.
5. What are the benefits of passwordless login?
Now that you know about the security benefits of passwordless logins, you’re probably wondering what other perks implementing a similar system will have for your company or organization.
Developers are constantly looking for best practices to make the login process quick and easy. You’re probably aware that one of the main causes of shopping cart abandonment—when people leave your form before confirming their transaction—is that users are forced to create an account in order to move forward.
While having an account is essential if organizations want to encourage their users to make repeat transactions, users are less likely to purchase again if they can’t remember their password.
Essentially, passwordless login gives users the best of both worlds: users can keep their payment information securely on file, saving them time in the future, and they won’t have to remember a long complicated password, which will encourage repeat transactions. Moreover, your users are more likely to make impulse purchases when the process is much easier.
6. Are there risks associated with passwordless login?
As previously mentioned, no authentication method is completely foolproof. That means passwordless login systems come with their own set of risks. But compared to the weakness of traditional login systems, the risks are relatively low.
Of course, as with any new system that your organization implements, you’ll have to go with a reputable vendor to make sure user data is processed and stored as securely as possible. As far as users go, there is still a chance that their accounts can be compromised. For example, if a hacker gains access to a user’s email account, the accounts using email authentication could be compromised. However, it’s important to note that the leading email providers tend to have the most advanced security features such as built-in 2FA, making this less than likely to occur.
Other passwordless login systems have their own set of risks and challenges. For example, hackers can access an account protected by biometrics by creating a master fingerprint using the most common characteristics, and facial scanners can be tricked with high-quality photos.
Each passwordless login option comes with its own set of vulnerabilities, just like each alternative comes with its own benefits as well. Before making a buying decision, it’s important to take a good look at the pros and cons to find the right solution for your website.
7. How user-friendly is passwordless login?
As passwords are becoming more and more obsolete, your users might already be familiar with several popular password alternatives. If you’ve ever signed up for a website using your Facebook or Gmail account, then you’ve used a form of passwordless login. Not to mention the fingerprint scanners embedded in many recent smartphones.
With that said, users already have some understanding of how the process works, so there is less of a learning curve. Additionally, experts stress how passwordless login systems don’t require any memorization. The tools a user needs to complete the login process are readily available.
Generally, the process requires only two to three steps and takes about the same amount of time as a traditional login process if not shorter! Without the hassle and responsibility of creating a strong password, users can conveniently log into their accounts feeling confident that their information is secure from unauthorized users.
Long story short, passwordless logins are extremely user-friendly because users are most likely familiar with the process. Plus, logging in with more passwordless security measures is easier and doesn’t take any longer than the traditional process.
Say Goodbye to Passwords
and
Hello to Secure Logins.
Go passwordless and delight your users with secure and seamless one-click login.
8. Which types of websites can use passwordless login?
Password login systems are completely universal, which means that any type of organization can use them. What’s more, passwordless login can be used for more than just a way to enter your accounts.
Passwordless Login for Businesses
Your company can use password alternatives for internal security, online users, or a combination of both.
Moreover, any account can be replaced with a secure password alternative. Passwordless login can be used to:
- Log in to an online account.
- Make secure payments to an e-commerce site.
- Sign up for a subscription or service.
By using passwordless login options, you’ll be able to keep your user’s information safe and enforce stronger security measures for your employees.
Passwordless Login for Nonprofits
Nonprofits and faith-based organizations can use passwordless login to make the donation process easier and more secure for their supporters.
When donors give to your nonprofit, they can save their payment information using a password alternative like email authentication. The next time a donor gives, the person will only complete three simple steps!
Both nonprofit and for-profit businesses alike can make use of powerful password-free authentication tools. By streamlining (and securing) internal and external operations, anyone who uses your site will be grateful.
9. How hard is it to implement passwordless login on my site?
Since there are several different types of passwordless login, the time and effort it takes to implement will vary. But for the most part, these systems can be easily implemented on your website.
Imagine that your organization wants to offer Swoop’s email authentication to your users. Swoop offers a free WordPress plugin that can be downloaded and running in minutes — even if your team has no coding experience. Further, if you’d prefer a more custom implementation, we offer step-by-step guides to assist you with a variety of programming languages within our handy Document Center.
As you can see, the process doesn’t require a lot of work, or money, on your part.
Alternatively, if your organization wants to use biometrics, the implementation process could take much longer. Not only will you need the software integrated into your website, but you’ll also have to ensure the program works with compatible devices. Plus, your users will need the necessary hardware on their own devices to be able to scan for biometric characteristics.
Implementing passwordless login will vary depending on the type of system you choose. Luckily, most of the hard work is completed by the provider’s development team.
10. How do I promote passwordless login to my users?
As with any new consumer-facing method or process, your users might have some hesitation. For example, individuals who have little-to-no experience using passwordless login systems may question its security as well as its ease of use.
If you want people to use your passwordless login system, you need to be able to put their concerns at ease and show them how it works.
Here are a few ways you can promote your passwordless login system:
- Create a video to post online. Create a video that demonstrates how the authentication process works. Whether you’re using email authentication or fingerprint scanning, showing your users all the steps will make them more familiar and comfortable with the process. You can post your video to social media or on your website.
- Highlight your new feature in your newsletter. Your regular newsletters or emails are the perfect place to let users know that your passwordless login system is up and running. Make sure to include resources where they can learn more about the process as well as a link to where they can log in.
- Engage with users on social media. After launching your passwordless login system, encourage your users to ask questions on Facebook and Twitter. That way, you can answer the concerns that matter most to your customers or donors and get them excited about your easy-to-use login process.
As you can see, there are countless ways you can promote your passwordless login system to users and make them feel comfortable using it. Users may be hesitant at first, but by demonstrating how to use the tool and answering your users’ questions, they’ll get on board in no time!
There you have it: a few of the most common questions about passwordless login systems answered. Hopefully, this information has helped you to determine if passwordless authentication is something your website should implement. (P.S.: we hope the answer is yes!)
For more information about passwordless login systems and ensuring a highly secure website for your users, check out these additional resources:
- Password Alternatives for Better Website Security: Are you looking for specific ways to get rid of troublesome passwords for your users? You’re in luck! This article takes you through the pros and cons of three of our favorite alternatives.
- A Modern Password: 6 Top Tips for A Secure Login Process. If you are stuck with a password-based authentication system, for whatever reason, make sure your passwords are as secure as can be with these top tips.
- Two-Factor Authentication: A Definitive Guide For Websites. Multi-factor authentication systems add an extra layer of security on any website. For example, you can add a passwordless method on top of a password-based authentication system.