Did you know that the average user has around 90 online accounts to manage? There are many different ways an individual can gain access to an account, but not all authentication methods were made equal. While password-based login systems are the most popular choice, they’re far from the best.
Here at Swoop, we think traditional login tools are huge liabilities for websites— both because they’re insecure and provide a terrible user experience. That’s why we’ve developed a more secure, token-based authentication service that can reduce the reliance on weak password systems. Take control of your login process and provide a better experience for your users!
If you’re a web developer or system designer, you’ll need to implement some token-based authentication into your site. Modern users have come to expect the more streamlined experience that tokens provide. Plus, they offer a level of security that simpler systems just can’t beat.
That’s why we’ve put together this helpful guide to token-based authentication. We’ll walk through some of the most common questions about this process and how it can improve your site:
- What is a token?
- What is token-based authentication?
- Why is token-based authentication better than a password?
- What are the different types of token-based authentication?
- How do I get started with token-based authentication?
Token-based authentication methods can dramatically improve online usability and security by providing a more streamlined and highly secure process. As a developer yourself, it’s your responsibility to provide users with the best and most secure experience possible. Use the list above to jump straight to what you need, or read along from the top. Let’s get started.

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
1. What is a token?
A token is a highly secure format used to transmit sensitive information between two parties in a compact and self-contained manner. Tokens are often used to strengthen authentication processes, whether that be within a website or application.
A typical token consists of three key elements:
- A header that defines the type of token and algorithm used.
- A payload that contains information about the user and other metadata.
- A signature that verifies the identity of the sender and the authenticity of the message.
When sensitive data is transmitted via token, users can rest assured knowing their private information is treated as such. This is crucial for any sort of payment information, medical data, or login credentials.
2. What is token-based authentication?
Token-based authentication is a web authentication protocol that allows users to verify their identity a single time and receive a uniquely-generated encrypted token in exchange. For a designated period time, this token is how users access protected pages or resources instead of having to re-enter their login credentials.
Here’s how the token-based authentication process works:
Token-Based Authentication
1. Login
The user enters their username and password.
2. Login Verification & Token Generation
The server verifies that the login information is correct and generates a secure, signed token for that user at that particular time.
3. Token Transmission
The token is sent back to the user’s browser and stored there.
4. Token Verification
When the user needs to access something new on the server, the system decodes and verifies the attached token. A match allows the user to proceed.
5. Token Deletion
Once the user logs out of the server, the token is destroyed.
The token proves you’ve been allowed in and allows you to view other resources and make further requests. This is an improvement from traditional processes that require users to verify their identities at every step.
This enables the website to add more layers of security without forcing you to prove you are who you are time and time again. Thus, the process works to improve user experience and security simultaneously.
3. Why is token-based authentication better than password logins?
Traditional passwords have one huge weakness: they’re human-generated. Human-made passwords tend to be pretty weak and easy to crack. We’ve all reused old passwords again and again because they’re easy to remember.
Not only that, but a password-based login system requires users to continuously enter and re-enter their credentials, essentially wasting valuable time. The traditional password-based login process looks something like this:
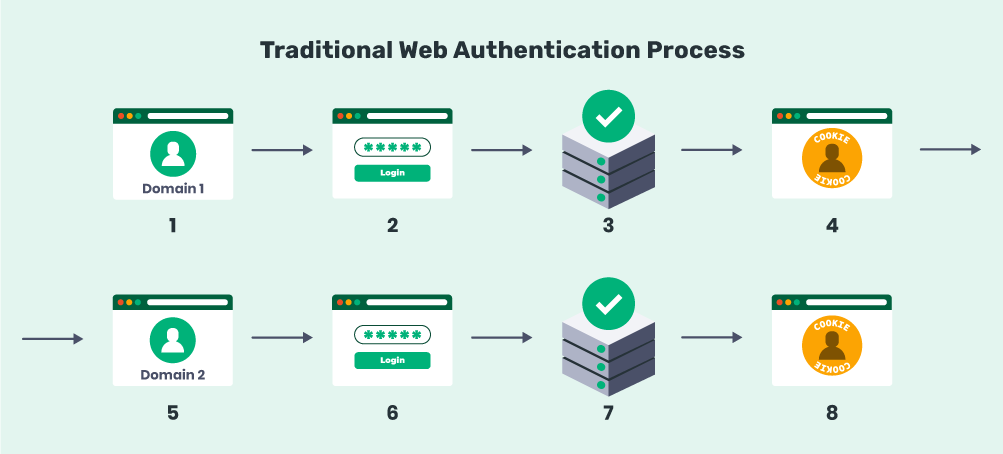
- The user arrives at the target domain.
- They enter their login credentials.
- The server verifies the match and lets them in.
- The user is authenticated to access that domain.
For steps 5-8, users need to repeat the entire process in order to access anything hosted on a different server, domain, or subdomain. Common examples include viewing or editing account details and beginning an eCommerce checkout.
So what’s wrong with this process? A few things. For one, it’s unintuitive and wastes the user’s time. Who wants to enter their credentials over and over again in order to complete multiple tasks? Every user has better things to do than waste their time on a repetitive and unnecessary process.
Plus, the login system above is likely already vulnerable because the password is weak to begin with! In this simple authentication setup, each login step is a weak link that’s open to attack.
So how does token-based authentication offer new solutions?
Token-based authentication is more secure.
Token-based authentication, on the other hand, uses ultra-secure codes to prove that you’ve already been authenticated. They’re specific to the user, the particular log-in session, and the security algorithm that the system uses. In other words, the server can identify when a token’s been tampered with at any step and can block access.
Tokens essentially act as an extra layer of security and serve as a temporary stand-in for the user’s password. Most importantly, tokens are machine-generated. Encrypted, machine-generated code is significantly more secure than any password you might create yourself. For example, our tools here at Swoop create digital tokens with 2,048-bit encryption that would take even the best hackers billions of years to crack.
Token-based authentication offers a streamlined process.
Rather than having to re-verify your identity every time you arrive at a new page, tokens are temporarily stored in the browser, providing you access to information on the domain for a specified time period. This allows you to jump from server to server or subdomain to subdomain without constantly being slowed by the authentication process.
For users, this allows you to easily navigate a website and efficiently find the resources you’re looking for. For developers, it keeps individuals on your site for longer by decreasing the risk that users become aggravated and click out.
When the user is finished with their browsing session, they simply have to log out and the stored token is destroyed forever. This way, users don’t risk leaving their accounts open to attack.
4. What are the different types of token-based authentication?
You probably have experience using token-based authentication methods, whether you realized it at the time or not. Here are a few common, everyday examples of token-based authentication you might see in the real world:
- Accessing an account from a one-time text or email link.
- Using a fingerprint or facial scanning methods to unlock a smartphone.
- Logging into a new web page using your Facebook login credentials.
Although unique usernames and passwords remain one of the most widely used authentication methods for websites and applications, token-based alternatives are quickly becoming a norm. Keep an eye out for the times you might be using a password alternative to access restricted resources!
There are many different ways a user can verify their identity using token-based authentication methods. How can you choose the best one for your website or web application? Let’s walk through some of the top user authentication processes!
Swoop authentication
Swoop’s secure token-based login system can help you eliminate passwords from your site once and for all. We have two different initial mechanisms for authentication—Magic Link™ and Magic Message™. Here’s a brief overview of each:
Magic Link™ utilizes an automatically generated link to provide highly secure password-free authentication to users. It’s the easiest way to improve security on your site and lose passwords in one simple step. The process looks like this:
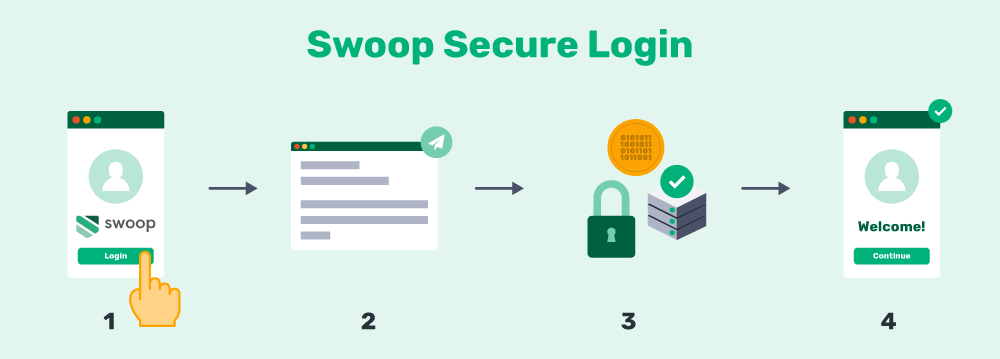
- Swoop’s Magic Link™ is sent to a user’s email to verify their identity.
- The user clicks the link from their email.
- The user’s credentials are verified and a token is created.
- The user is authenticated.
Our Magic Link™ authentication system is becoming increasingly common, but the downside is that it requires a user to switch between the authentication service and a mail client to find and follow the link. On the other hand, we also offer an even better mechanism with our Magic Message™ that does a similar function in only two simple clicks.
Here’s how Magic Message™ works:
- The user is redirected to the Swoop service via the OAuth 2.0 protocol for authentication.
- From a browser window, the user pushes the “Send Magic Message™” button: The button activates a mailto link, which generates a pre-written email for the user to send.
- The user sends the email: This is where the magic happens. Once the email is sent, the outgoing email server generates and embeds a 1024/2048 bit, fully encrypted digital key into the header of the email. Swoop’s authentication server follows the public key cryptographic procedure to decrypt this key. Each email sent receives a unique key for that message. The level of security for these encrypted keys is beyond comparison to traditional passwords.
- The user is logged into their account: When the key decrypts and passes all layers of verification, the Swoop authentication server directs the website to open the user’s account and begin a session. This all takes place in a matter of seconds and makes for an extremely streamlined user experience.
Basically, this gives you the option to replace passwords entirely. Swoop’s token-based authentication is an ideal solution for websites, web apps, or other online resources that need to be protected.
Say Goodbye to Passwords
and
Hello to Secure Logins.
Go passwordless and delight your users with secure and seamless one-click login.
Biometric authentication
Biometric authentication techniques use a concrete, unchangeable biological characteristic in place of a machine-generated token. This variation of token-based authentication has become more popular in recent years, but it still has a long way to go.
Biometric authentication processes can be fooled, so they’re not currently as secure as an encrypted digital key. However, they’re still a great security option for hardware, like phones and computers, since the device doesn’t necessarily need internet access in order to verify a match.
Biometric tokenization can take the authentication process a step further by storing users’ sensitive biological data in the form of unique and randomized tokens. This makes it significantly harder for cybercriminals to gain access to critical information. Because data is divided and stored in a variety of locations, it’s less likely that a hacker is able to fake the biometric characteristics required for authentication.
Social sign-in authentication
This is a common authentication technique that relies on tokens. You’ve likely seen this before when a website gives you the option to log in via an existing social media account or when an application wants to post something to your social profile on your behalf. This process is also called open authorization.
Basically, this process works by creating a uniquely-generated token that only the website and the social media platform can decode. The token serves as an intermediary. Since the token acts as a secure stand-in for a password, this authentication option is useful for when you don’t necessarily want to share your login credentials with multiple apps or sites.
5. How do I get started with token-based authentication?
Previously, implementing a token-based security system required a lot of work from a developer or team of developers. You can still use an in-house team or tech consultant to custom-develop a token system, but this route can be costly and time-consuming.
Easier options now exist that let any site or web app use ultra-secure tokens to authenticate users. For instance, Swoop can be set up on just about any site in as little as 5 minutes. Here’s how the basic implementation process works:
- Integrate with a plugin/app (such as a WordPress plugin) or write a custom integration.
- Specify the login link that users will click to initiate the token-generation process.
- Specify the endpoint link that the authentication tool will redirect users to once their token is verified.
- Set up a trigger for users to begin the process, like placing a ‘Log in with Swoop’ button.
It’s as simple as that! Thanks to carefully crafted authentication software like Swoop, it’s never been easier to implement passwordless authentication alternatives across your website.
Digital tokens are the perfect way to reduce your website’s reliance on passwords. It’s easy to take token-based authentication for granted, but as online users, it’s one of the key features involved in a secure and intuitive online experience. So if you’re looking to make drastic user improvements to your website, be sure to explore your options and get to know some of the top token-based password alternatives available.
Don’t forget to keep educating yourself, too! Here are a few related resources we suggest checking out:
- A Modern Password: 6 Top Tips for A Secure Login Process. One of the many benefits of using tokens is that it keeps your users’ passwords protected. Learn more about how you can improve your website’s password security with our ultimate guide.
- Top 3 Password Alternatives for Better Website Security. If security is your main objective, you might want to consider using password alternatives. Read more to learn why passwords aren’t the best at keeping information secure.
- Security Authentication vs. Authorization | What’s the Difference? These two terms are commonly confused, although the differences are quite important. Check out our guide that compares authentication and authorization in web practices!