We spend more of our time online than ever before, constantly creating new accounts on all kinds of websites and applications. And while web developers are always looking for new and improved ways to promote security throughout their sites, the specific ways in which we log in haven’t changed very much over the years.
The truth is that traditional username/password logins aren’t very secure, especially since many users continue to use weak and compromised credentials. Further, websites don’t enforce truly effective password creation guidelines, opting to favor ease-of-use over security.
There are certain ways you can start to move your site’s login process in the right direction, making it more convenient and secure for your users. Here we’ll cover six modern best practices for ensuring your login process is as effective as possible:
- Let users view their modern password.
- Notify users of suspicious login behavior.
- Limit the number of login attempts.
- Ditch modern password strength checkers.
- Update modern password requirements.
- Explore modern password alternatives.
Usernames and passwords are still the most common way we gain entry to our online accounts, but are they the best way? (The answer is no, but we won’t get into that yet. We’ll walk through some innovative login solutions at the end of this article.) For now, let’s dive into some of these best practices for a more secure username and password login system.
1. Let users view their modern password.
When it’s time to log into an account, we’ve all seen our password appear as a few dots on the screen. Replacing the characters with dots is a process that most websites use to keep your credentials secure from wandering eyes, but it also opens up a new range of vulnerabilities.

While this is a well-intentioned idea that can certainly come in handy sometimes, it’s important you provide the option to turn this feature off, allowing users the option to view their passwords as they type.
If you’re asking yourself why, here are two main reasons.
For security purposes
Since users aren’t able to see if they’ve made any mistakes, they’re more likely to create a simple password to avoid getting it wrong.
Think about it like this: with a long, complex password, you’ll have to hope that you get all the characters right or you’ll have to retype your credentials all over again, which could make the login process very time-consuming. Instead of unintentionally encouraging users to create “easy” credentials, simply give them the option to show their passwords as they type.
This allows users to double-check that their passwords are error-free not only when they log in but also as they create a new account.
For UX purposes
Imagine you’re typing out your password to gain access to a social media account, and your finger slips. You’re not sure if you hit the right key! And because all it shows you is those little dots, you have to erase your entire password and try again. We’ve all been there, and it can be extremely frustrating from a usability standpoint.
If you had the option to see your password on the screen, you could have easily determined whether or not you’d mistyped— and only adjust any necessary characters. Instead, you’ll have to completely retry your password as many times as it takes to get it right.
Users gravitate toward simple passwords, partly because they’re easy to remember but also because they don’t want to risk typing the wrong thing. Offering the simple option to see the password removes a major UX and security obstacle! However, it is useful to be able to disable the feature in situations where they don’t want their password to be seen— in case of those prying eyes.
Say Goodbye to Passwords
and
Hello to Secure Logins.
Go passwordless and delight your users with secure and seamless one-click login.
2. Notify users of suspicious login behavior.
Monitoring your site’s security should be a continuous top priority. After all, letting users know when you suspect that their accounts might be compromised is the only responsible way to steward their sensitive data. When you’re carefully monitoring suspicious web activity, you’ll be more likely to catch and put an end to an issue before it gets out of control.
For example, it’s important to notify users of suspicious password and username login attempts. By notifying users early, you’ll prevent more accounts from becoming compromised and keep sensitive information safe from unauthorized users.
Users should be informed of a potentially compromised account if:

- There have been multiple login attempts to their account in a short period of time.
- Your organization experienced a data breach.
- Significant changes have been made to the user’s account settings.
- A password change request has been made.
- An account password has been changed.
The best way to notify users is through their linked email address or text message. In addition to notifying users of this activity, you should also provide them with suggested steps to make their accounts more secure.
For example, encourage users to change their credentials using up-to-date guidelines on what makes a secure password. Plus, if your website offers passwordless login alternatives, be sure to promote that as an easier and safer way to manage an account!
If you suspect that a user’s account is in serious risk of losing their sensitive information, place a hold on the account until you’ve received additional authentication from the user. By being overly cautious with your users’ information and monitoring the changes that are being made, any unauthorized access can be nipped in the bud before the hacker causes serious damage.
Plus, you’ll establish trust with your users by showing them that you’re putting security first. Not only will this help make your product or service stand out, but it also reduces the odds that your company becomes the victim of a data breach. Users are always looking for the most secure option, while hackers will likely avoid those. It’s a win-win!
3. Limit the number of login attempts.
When it comes to suspicious activity, there are also a few ways to shut these potential scammers down before they are ever granted access to an account.
One of the strategies that hackers use to crack a password is called a brute-force attack. Basically, this means that the hacker will use software to run through every password combination until it gets a match. Since these computer programs can run through billions of guesses every second, the process can take anywhere from a couple minutes to several years depending on the strength of the password in question.
If your website doesn’t have any restrictions on the number of times a user can attempt to log in, this can make the hacker’s job much easier.
Therefore, it’s important to set limits on the number of login attempts and password reset requests per user. To implement this strategy, be sure to set protocols in place determining when to restrict access to an account or take additional steps to prevent malicious behavior on your site.
Here a few things you should keep in mind:
- Give users a maximum of 5 password guesses per minute. Let’s face it: we’ve all forgotten our password and sometimes we need a couple of tries to get it right. However, this limitation will flag hackers using brute-force attack computer programs. After the first 5 attempts, simply block the account for 10 minutes or so.
- Restrict the number of guesses by IP address to 20 per minute. The limit for IP addresses should be higher because shared offices might use the same IP address and have multiple users trying to log in on your website. If you notice a high volume of login attempts from the same IP address frequently, you might need to investigate and/or make the executive decision to block that IP.
- Accept a maximum of 2 password reset requests per account and 5 per IP address. Giving users more opportunities to reset their password can lead to less secure accounts. For instance, a hacker may make several requests to determine which email is linked to the account.
Of course, these are just suggestions. Your organization should adjust these guidelines to fit your specific needs. As an added step, if an account is blocked for any of the reasons above, it’s important to send the user an email notifying them of the situation. That way, if the attempts weren’t made by those users, they can take the next steps to protect their accounts.
4. Ditch modern password strength checkers.
A popular way for users to test the strength of their passwords is through online checkers like How Secure Is My Password, Password Meter, and My1Login. Often, you’ll see similar tools on websites when you create a new account. Users can type their passwords into the tool and have it rated on a scale of very weak to very strong. Sometimes these checkers measure strength using the time it would take to crack the password.
Unfortunately, password strength checkers aren’t the best way to judge security because they’re inconsistent and encourage users to create credentials that follow a guessable pattern. Plus, these tools can be inconsistent in their results or use outdated password security standards, giving users a false sense of security. Instead, organizations should focus on educating users about strong passwords rather than enforcing guidelines.
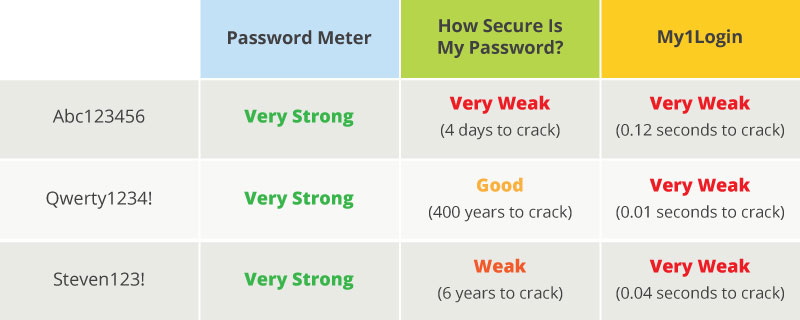
As you can see in the image above, some passwords that are considered okay or even strong are actually very weak. This occurs because there is no set standard on what makes a secure password. Plus, many password checkers include standards like:
- Include at least one uppercase letter.
- Use numbers and symbols.
- Create a password of up to 8 characters.
These requirements often lead to very formulaic passwords like “Jessica1234!” that are quite easy for hackers to guess based on typical user patterns (even if they meet all the criteria for the strength checker). Instead of using specific requirements, companies should focus on providing users with universal strategies that make passwords stronger.

1-Click Login is a simple & secure password-free authentication service.
With our patented technology, your website can improve security & increase customer conversion by removing passwords.
5. Update modern password requirements.
How can you encourage users to create better passwords?
First, your organization needs to stay updated on current password security recommendations. As new password-cracking technology is created, these recommendations can change from day to day.
Instead of giving users a set of requirements that must be included in their password, provide recommendations based on the most updated information.
For instance, The National Institute of Standards and Technology (NIST) often publishes new password security guidelines. Here is what their latest report suggests:
- Websites shouldn’t require users to change their credentials frequently.
- Users should create random passwords as they’re more secure.
- Longer passwords should be encouraged.
- Organizations shouldn’t enforce composition rules like adding an uppercase letter, number, etc.
In addition to these guidelines, organizations should also run any new passwords through a system that checks for the most commonly used passwords and credentials that have already been breached. For instance, if a user tries to create an account using the password “123456,” the system will tell the user to choose a different password.
Did you know that a shocking 98% of accounts can be accessed using 10,000 of the most common passwords? By preventing users from creating accounts with these passwords, you’re encouraging them to make stronger credentials and protect their sensitive information. That way, you can protect individual users and your overall organization at the same time.
6. Explore modern password alternatives.
So what is the answer to the modern password dilemma? It seems as if every password comes with its own set of vulnerabilities, leaving your organization and its users open to attack.
That’s why passwordless authentication is becoming an increasingly popular choice, both by web developers and users.
If your organization wants to take its login game to the next level, you should definitely consider password alternatives. While there are several different options, the core process works very similarly to two-factor authentication (where a key code is sent to your phone or email). The only difference is that no password is required at any step in the process!
Let’s take a look at two of the most common types of passwordless authentication.
Biometrics
If you have a cell phone that lets you unlock your screen with a fingerprint or facial recognition, then you’re already familiar with biometrics. From fingerprint, facial, and iris scanning to DNA screening, biometrics allows users to gain access to their accounts using their own biological traits.
Despite its many perks and conveniences, biometric authentication still has a few notable security vulnerabilities. An overview of how these systems work can help provide more context.
First, biometrics is costly to implement and can only be used by people that have a compatible device. In order to get operating, organizations have to purchase expensive technology and encourage users to purchase the necessary tools for it to function.
Additionally, recent research shows that replicating fingerprints (while difficult) is possible. Smartphone fingerprint scanners actually record multiple images of portions of your fingerprint. If your finger matches any of these images, you’re granted access. By creating a “master print” with traits common to most fingerprints, cybercriminals have been able to gain access to other people’s accounts. Even face scanning technology can be tricked with a high-quality photo.
Lastly, if another person does access your account, users can’t change their credentials like they would a traditional password. It’s not like you can just get a new fingerprint!
Email Authentication
Email authentication is one of the most universal and cost-effective passwordless login systems to implement— and anyone with an email account can use it.
The process works very similar to websites that let users log in with their Facebook account, so the process is already familiar to most users as well.
Here’s how our Magic Message works:
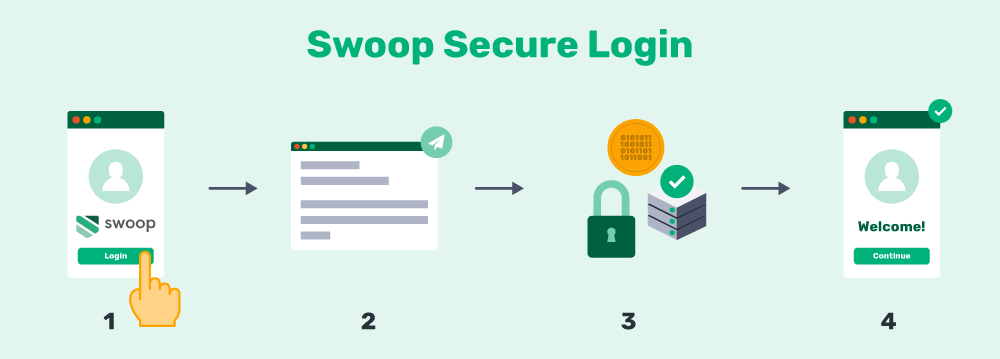
- The user is redirected to the Swoop service via the OAuth 2.0 protocol for authentication.
- From a browser window, the user pushes the “Send Magic Message” button: The button activates a mailto link, which generates a pre-written email for the user to send.
- The user sends the email: This is where the magic happens. Once the email is sent, the outgoing email server generates and embeds a 1024/2048 bit, fully encrypted digital key into the header of the email. Swoop’s authentication server follows the public key cryptographic procedure to decrypt this key. Each email sent receives a unique key for that message. The level of security for these encrypted keys is beyond comparison to traditional passwords.
- The user is logged into their account: When the key decrypts and passes all layers of verification, the Swoop authentication server directs the website to open the user’s account and begin a session. This all takes place in a matter of seconds and makes for an extremely streamlined user experience.
At Swoop, we use a unique code attached to every email to verify the user’s identity. Essentially, this method prevents hackers from gaining access to your account because they’ll need the credentials to your email as well. Even if they get past the first security measure, the system will flag any usual behavior and request a second authentication method via text message.
With several ways to create a modern passwordless login, your organization can eliminate the need for a password and create stronger accounts.
Hopefully, these tips have inspired you to update your password and username login system so that the process is more secure and convenient. Our top suggestion, of course, is to look into top passwordless authentication options that provide valuable benefits to both you and your users.
If you want more information on password security, check out these additional resources:
- Why Your Website Should Utilize Passwordless Authentication. There are plenty of reasons why organizations should start using passwordless authentication. Learn more about the many advantages with this article.
- Passwordless Login | The Internet’s Future in 8 Questions. Still have questions about email authentication or biometrics? This article answers some of the most frequently asked questions about passwordless authentication.
- Ultimate Guide to Two-Factor Authentication Solutions. One way to protect sensitive information on your website or application is by implementing two-factor authentication. Check out our comprehensive guide to learn more.